Prerequisites
As prerequisites you will need the following:- If you are setting up SSO with a self-hosted GitLab, make sure you have Admin permissions on that GitLab installation, or work together with the administrator.
- If you are setting up SSO with GitLab SaaS (gitlab.com), it is advised to create the OIDC application in a group, so please make sure you have Group Admin permissions on that group.
Create an OIDC application
The OIDC application allows you to integrate with Ona.- Navigate to Groups > My Awesome Group > Settings > Applications (for SaaS) or Admin Area > Application (for self-hosted).
- Click the Add new application button.
-
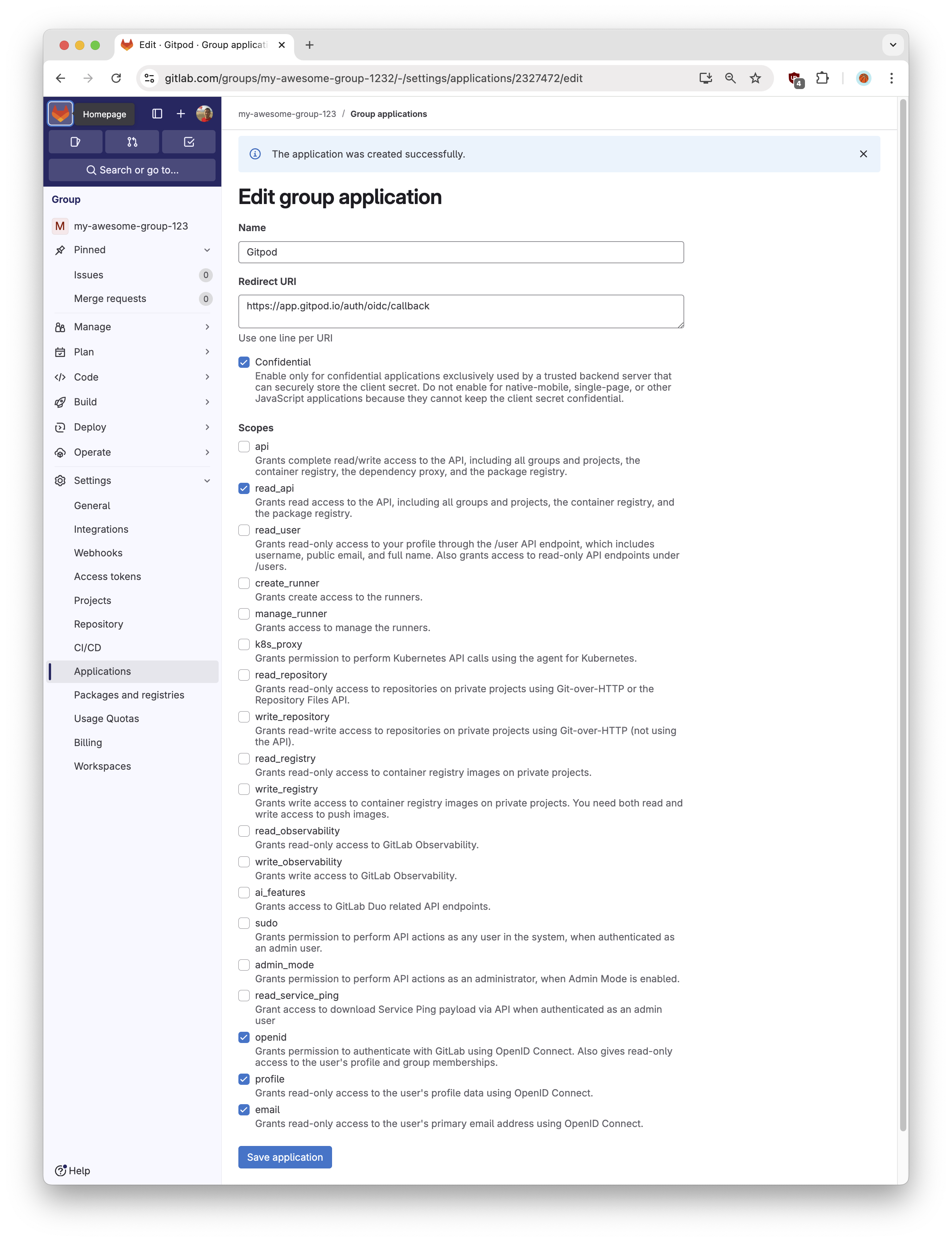
Configure the OIDC application by filling out the form:
- Name: Ona
-
Redirect URI:
https://app.gitpod.io/auth/oidc/callback -
Confidential:
Yes -
Scopes:
read_useropenidprofileemail
Save Applicationbutton.
-
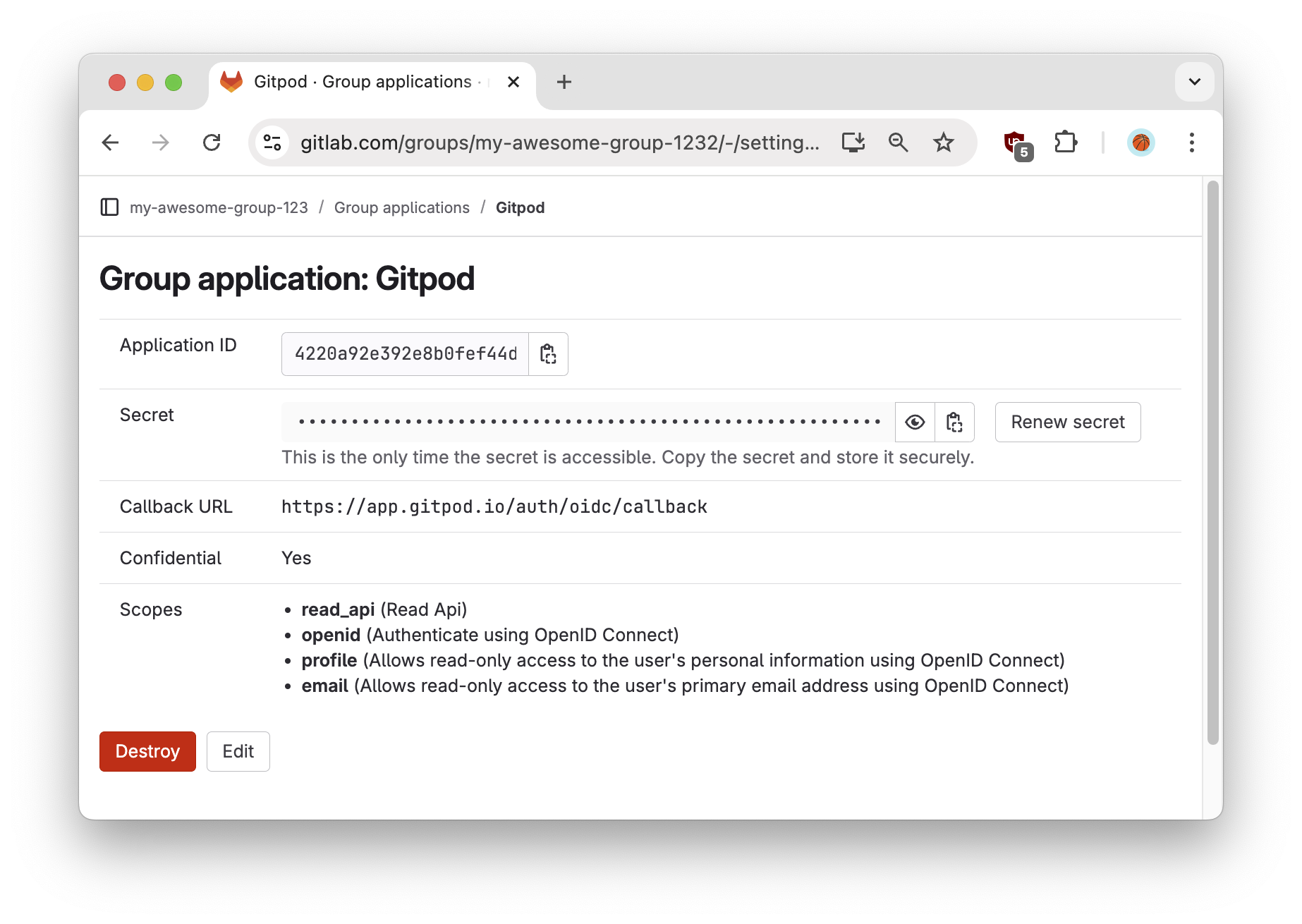
Obtain the Client ID & Client Secret from the following confirmation screen, which you’ll need for the Ona SSO configuration in the following step. This is how to interpret the information:
- Application ID: Client ID
- Secret: Client Secret
-
Which Issuer URL to use?
-
For self-hosted GitLab:
https://your-gitlab-installation.org -
For GitLab Saas:
https://gitlab.com
-
For self-hosted GitLab:
- Continue with the SSO configuration in Ona: Clicking Save & Test