Requires Core or Enterprise plan.
- Changes take effect immediately for new actions
- Existing environments are not affected
- Administrators can override certain policies
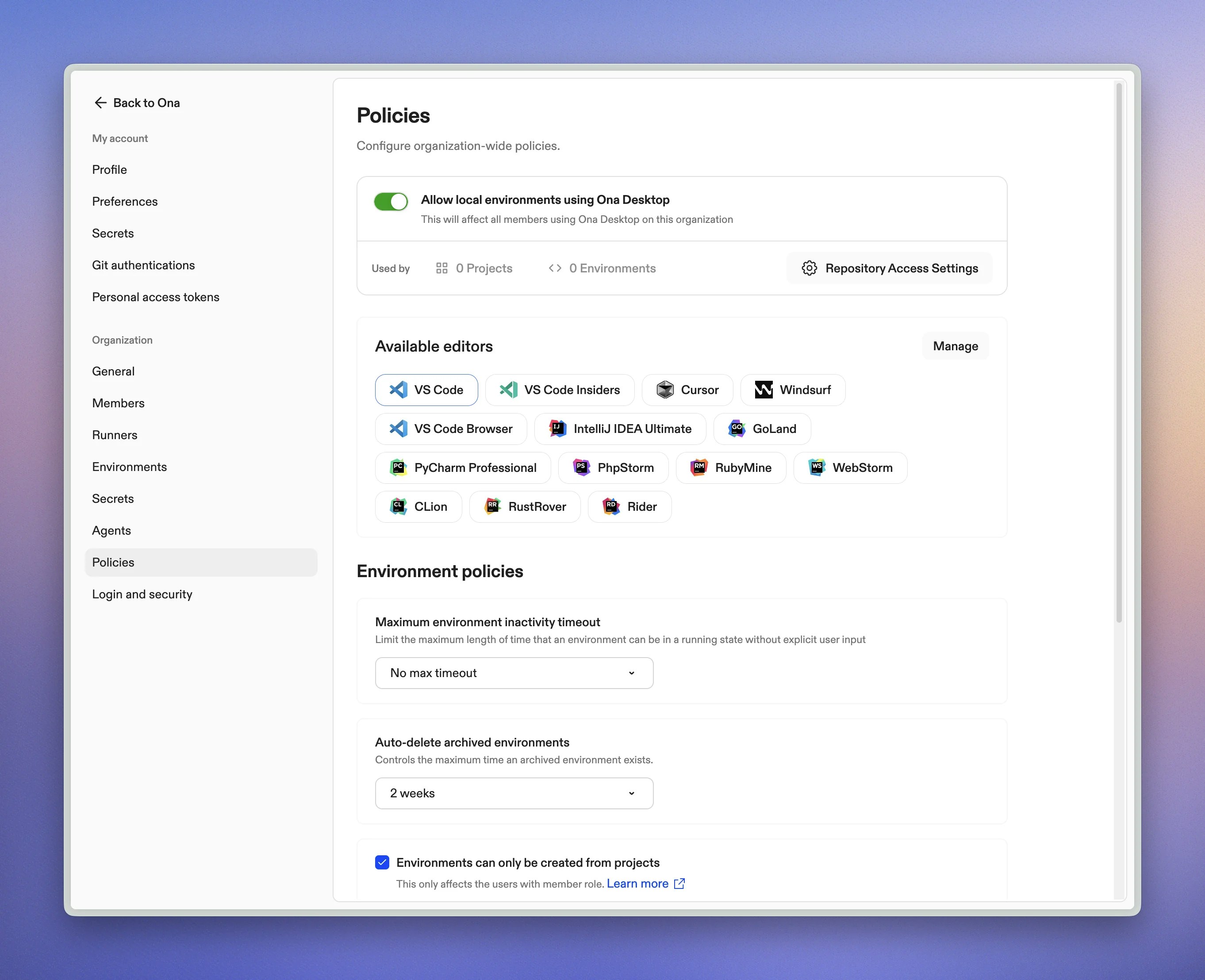
Available policies
| Policy | Purpose |
|---|---|
| Editor restrictions | Standardize which editors and versions your team can use |
| Environment timeout | Limit auto-stop timeout options |
| Environment limits | Cap total and concurrent environments per user |
| Environment and project creation | Restrict project creation to admins; members must use existing projects |
| Port sharing | Control user-initiated port exposure from environments |
| Default image | Set default devcontainer image |
| Auto-delete | Set retention period for archived environments |
| Security agents | Deploy CrowdStrike Falcon to all environments |
Looking for default environment image settings? See Default image policy.
Tracking changes
All policy changes are recorded in audit logs, including who changed what and when.Best practices
- Start gradually: Begin with moderate limits, inform your team, adjust based on usage
- Review regularly: Check usage patterns quarterly or after team changes
- Balance security and productivity: Don’t over-restrict; use project-based creation for control without friction