Requires Enterprise plan. Contact sales for access.
Overview
The setup involves two main steps:- Register the custom domain in your organization settings
- Configure cloud infrastructure to route traffic to the Ona management plane
- AWS: Uses VPC Endpoints and Network Load Balancer
- GCP: Uses Private Service Connect (PSC) and regional HTTPS Load Balancer
Prerequisites
Before you begin, ensure you have:- Admin access to your Ona organization settings
- Single Sign-On (SSO) configured - Custom domains require SSO to be set up. See the SSO documentation for setup instructions.
- A registered domain name (e.g.,
ona.example.com)
- AWS
- GCP
- An AWS account with appropriate permissions
- An AWS Certificate Manager (ACM) certificate with Subject Alternative Names (SANs) covering both:
- Main domain:
ona.example.com - VSCode subdomain:
vscode.ona.example.com
- Main domain:
About the VSCode subdomain: The
vscode subdomain (e.g., vscode.ona.example.com) serves a static VS Code Web application. This static content has no access to user data, source code, or any other resources unless the user is authenticated. Authentication is required before any user-specific data becomes accessible.Step 1: Register custom domain with Ona
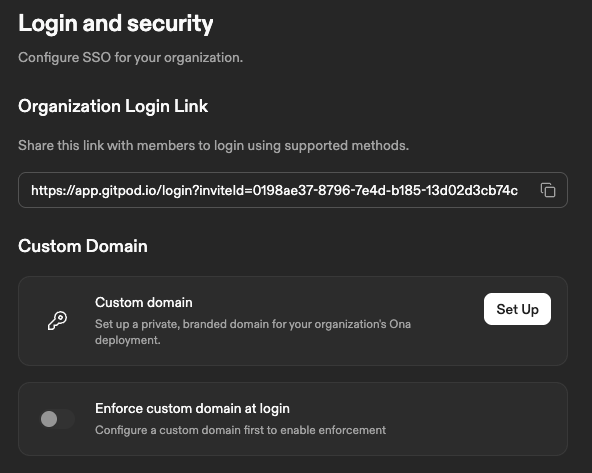
Register your custom domain name with the management plane through the Ona dashboard.- Navigate to Settings → Organization → Login and security
- Click Set Up in the Custom Domain section
Configure domain
Select your cloud provider (AWS or GCP) and enter the required information:- AWS
- GCP
- AWS Account ID: The 12-digit AWS account ID where you will set up the infrastructure (Load Balancer, VPC Endpoint). Find this in the AWS Management Console under My Account.
- Domain name: Your custom domain (e.g.,
ona.example.com).
Note: The AWS account ID you specify here must match the account where you create the VPC Endpoint. This is validated when requests come through your custom domain.
Step 2: Configure cloud infrastructure
Choose your cloud provider and follow the corresponding setup instructions.- AWS
- GCP
Now that the domain is registered with Ona, you need to set up the AWS infrastructure to route traffic from your domain to the Ona management plane.
2.1 Prepare your certificate
Ensure you have an AWS Certificate Manager (ACM) certificate that covers both your custom domain and the VSCode subdomain. This certificate will be used for TLS termination on the Load Balancer.Your certificate must include both domains as Subject Alternative Names (SANs):ona.example.comvscode.ona.example.com
2.2 Create security groups
Create two separate security groups: one for the Network Load Balancer and another for the VPC endpoint.Load Balancer security groupCreate a security group with the following rules:- Inbound: HTTPS (443) from your desired source (e.g., your corporate network, internet).
- Outbound: HTTPS (443) to the VPC Endpoint security group (to be created below).
- Inbound: HTTPS (443) from the Load Balancer security group (created above).
- Outbound: All traffic (or as per your security requirements).
2.3 Create VPC endpoint
Create a VPC Endpoint to connect to the Ona management plane service.Configuration- Navigate to VPC Console → Endpoints → Create Endpoint
-
Service Configuration:
- Service category: Select
Endpoint services that use NLBs and GWLBs. - Service name:
com.amazonaws.vpce.us-east-1.vpce-svc-00fa18d41fdd25cad. - Click Verify service.
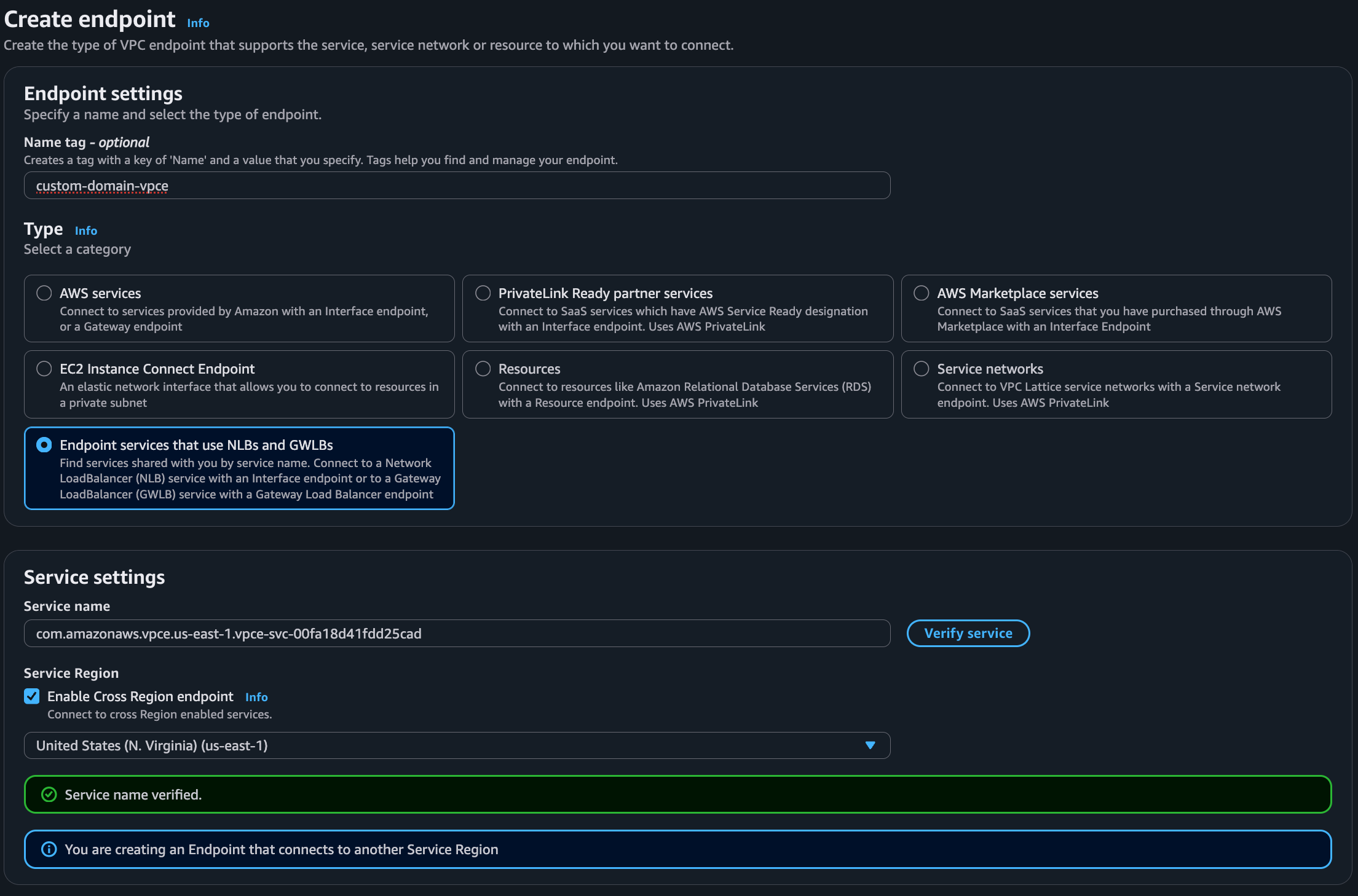
⚠️ Important: If you are in a region other than
us-east-1, you must:- Enable cross-region VPC endpoint.
-
Specify
us-east-1as the service region. -
The VPC endpoint service is available in the following Availability Zones:
- Service category: Select
-
VPC and Subnets:
- Select the VPC and subnets where you want your VPC endpoint to be created.
- Select at least 2 Availability Zones for high availability.
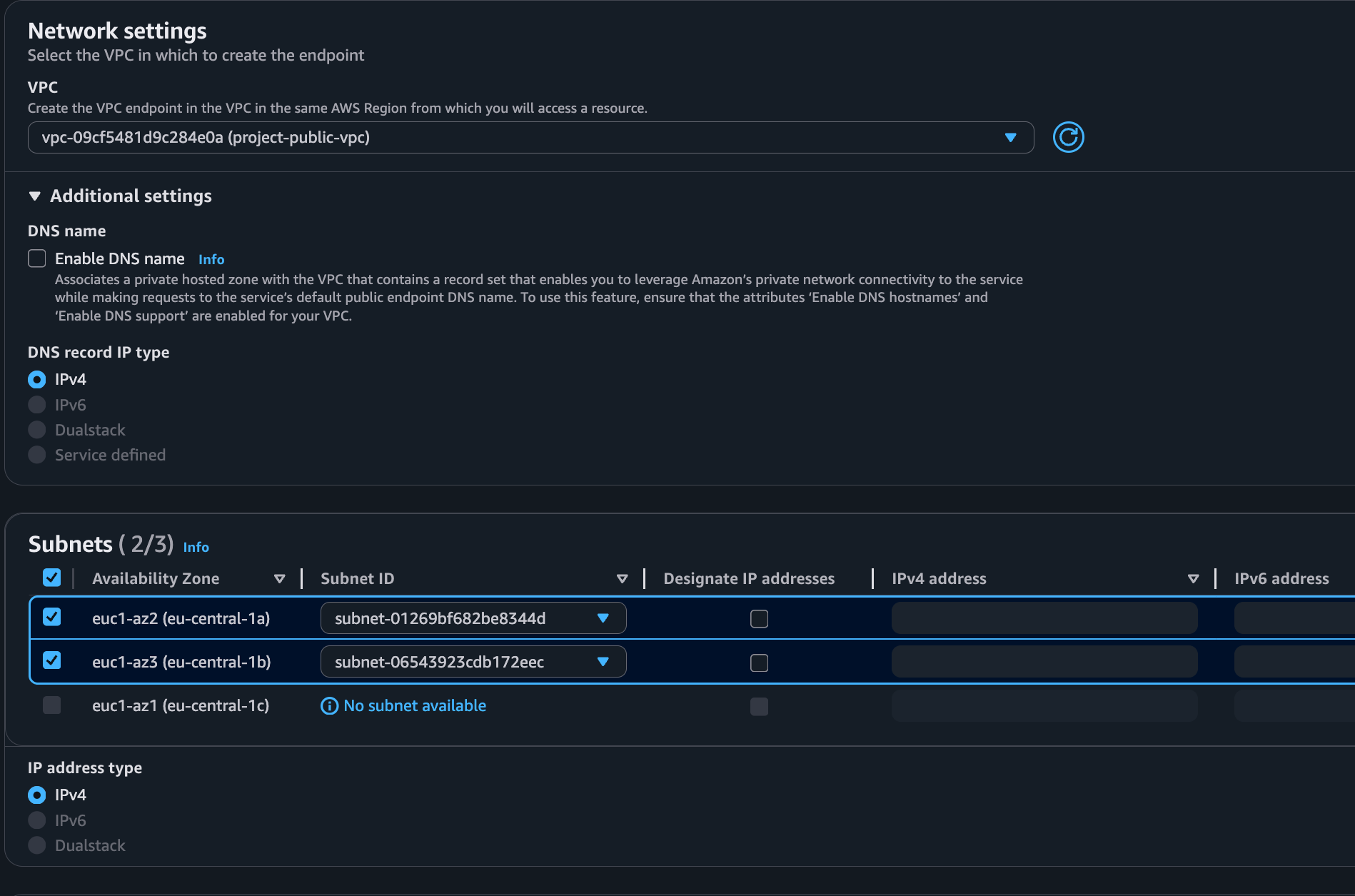
-
Security Groups:
- Select the security group created earlier for the VPC endpoint.
- Create Endpoint and wait for it to become Available.
-
Note the Private IP Addresses:
- Once the VPC Endpoint is available, navigate to the Subnets tab.
- Note down all the private IP addresses assigned to the endpoint (one per subnet/AZ).
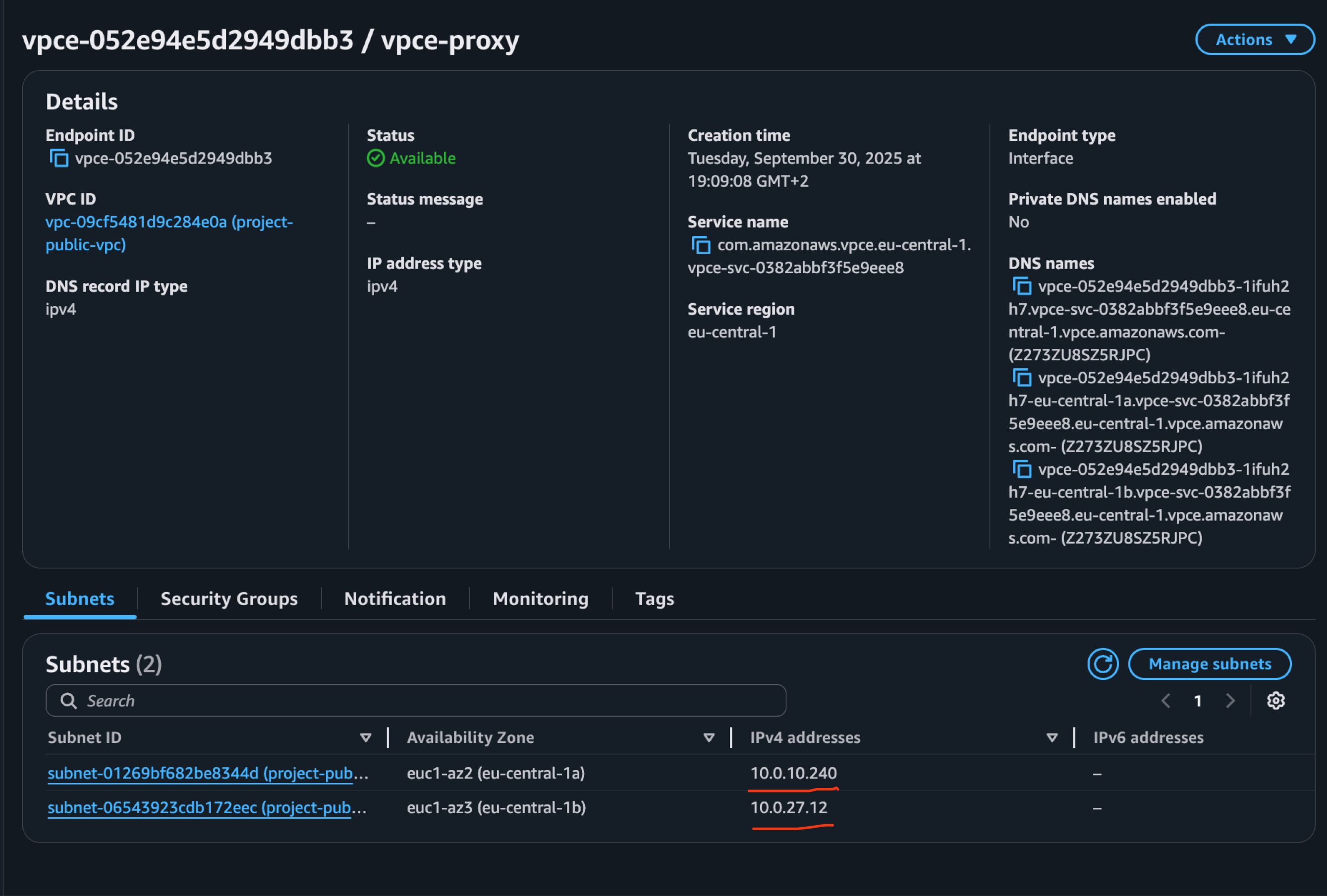
2.4 Create target group
Create a Target Group to route traffic from the Load Balancer to the VPC Endpoint.Configuration- Navigate to EC2 Console → Target Groups → Create Target Group
-
Basic Configuration:
- Target type: IP addresses.
- Target group name: Give it a descriptive name (e.g.,
ona-vpce-targets). - Protocol: TCP.
- Port: 443.
- VPC: Select the same VPC.
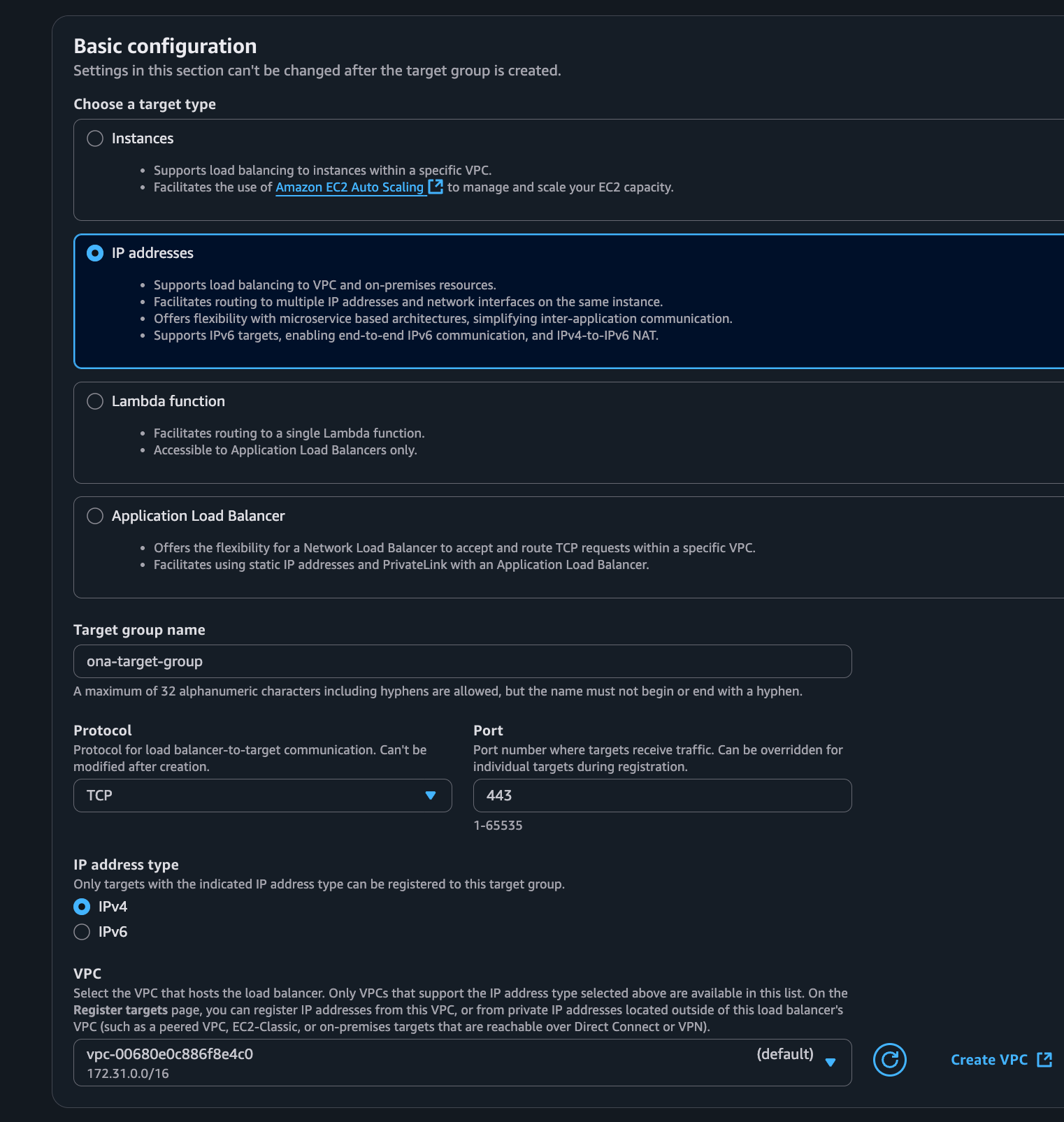
-
Health Checks:
- Protocol: TCP.
- Leave the default health check settings.
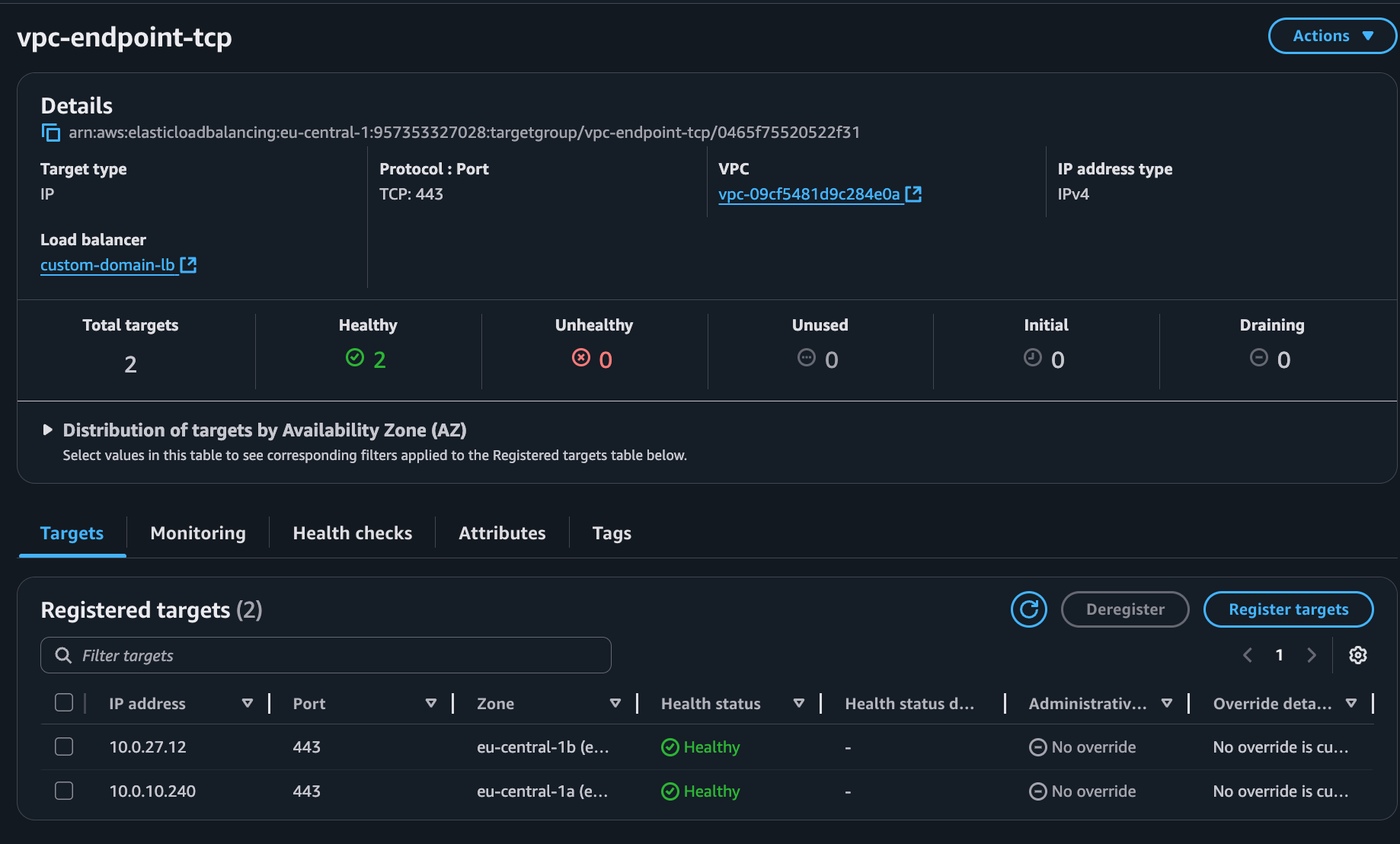
-
Register Targets:
- Click Next.
- Add each private IP address from the VPC Endpoint (noted in step 2.3).
- Port: 443 for each IP.
- Click Include as pending below.
- Click Create target group.
2.5 Create Network Load Balancer
Create a Network Load Balancer (NLB) to handle incoming traffic.Configuration- Navigate to EC2 Console → Load Balancers → Create Load Balancer
-
Choose Load Balancer Type:
-
Select Network Load Balancer.
-
Select Network Load Balancer.
-
Configure Load Balancer:
- Name: Give it a descriptive name (e.g.,
ona-custom-domain-lb). - Scheme: Choose Internal or Internet-facing based on your access requirements.
- IP address type: IPv4.
- VPC: Select the VPC of your VPC endpoint.
- Availability Zones: Select the same Availability Zones chosen for the VPC endpoint (must be at least 2).
- Name: Give it a descriptive name (e.g.,
-
Select the Security Group:
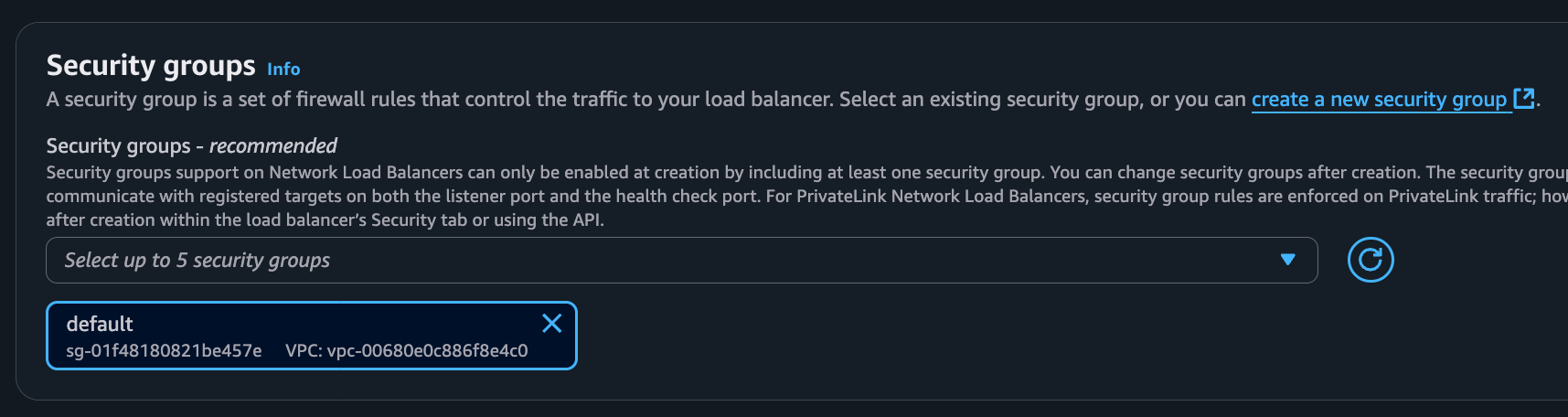
- Select the security group created earlier for the load balancer.
-
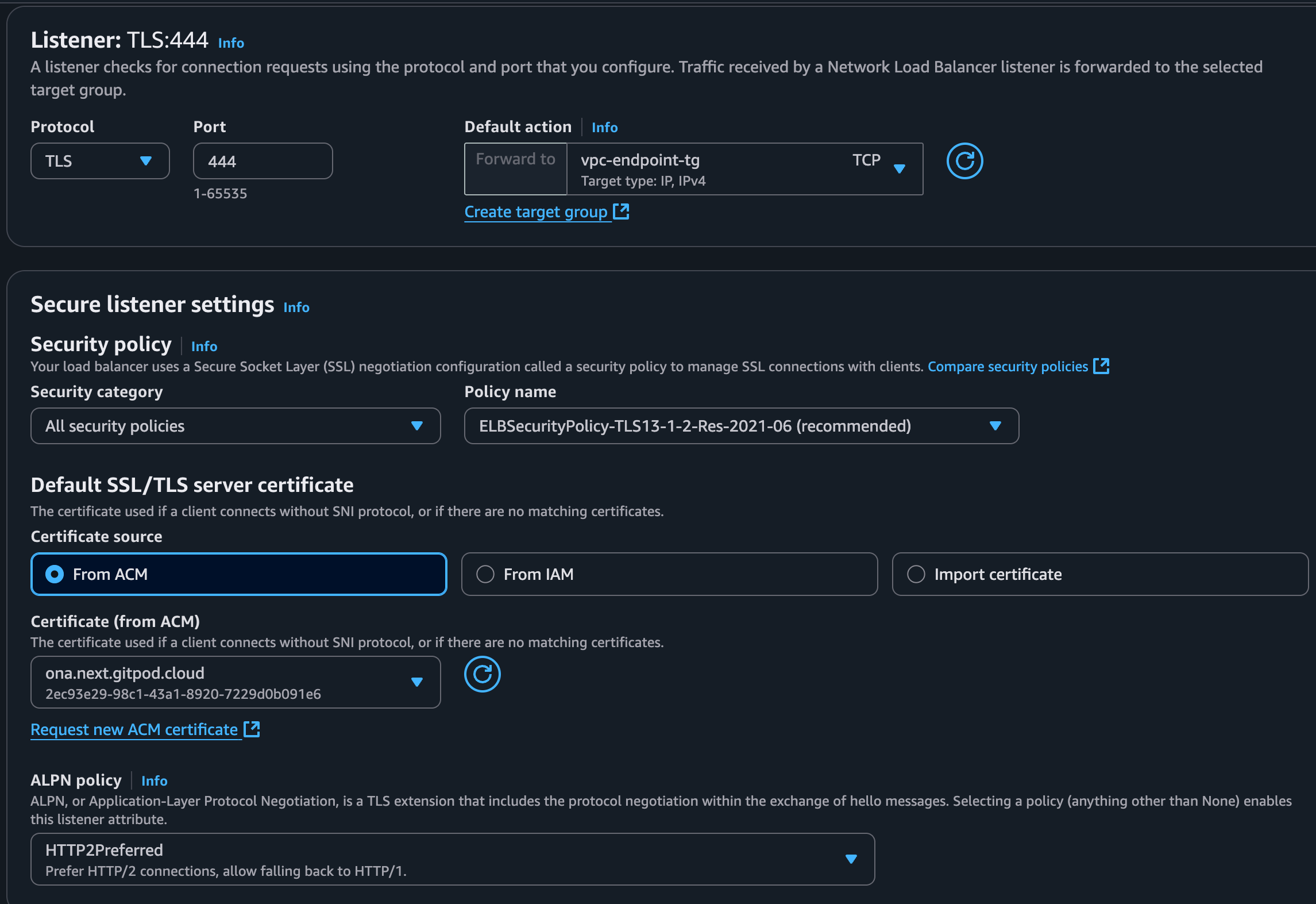
Configure Listener:
- Protocol: TLS.
- Port: 443.
- Default action: Forward to the target group created in step 2.4.
- Default SSL/TLS server certificate: Select the ACM certificate you prepared.
- ⚠️ ALPN policy: Select HTTP/2 preferred as the ALPN policy. This is important for optimal performance when connecting to the management plane.
- Create Load Balancer.
Step 3: Configure DNS
Point your custom domain to the Load Balancer.- AWS
- GCP
You need to create two DNS records: one for the main custom domain and one for the VSCode subdomain.
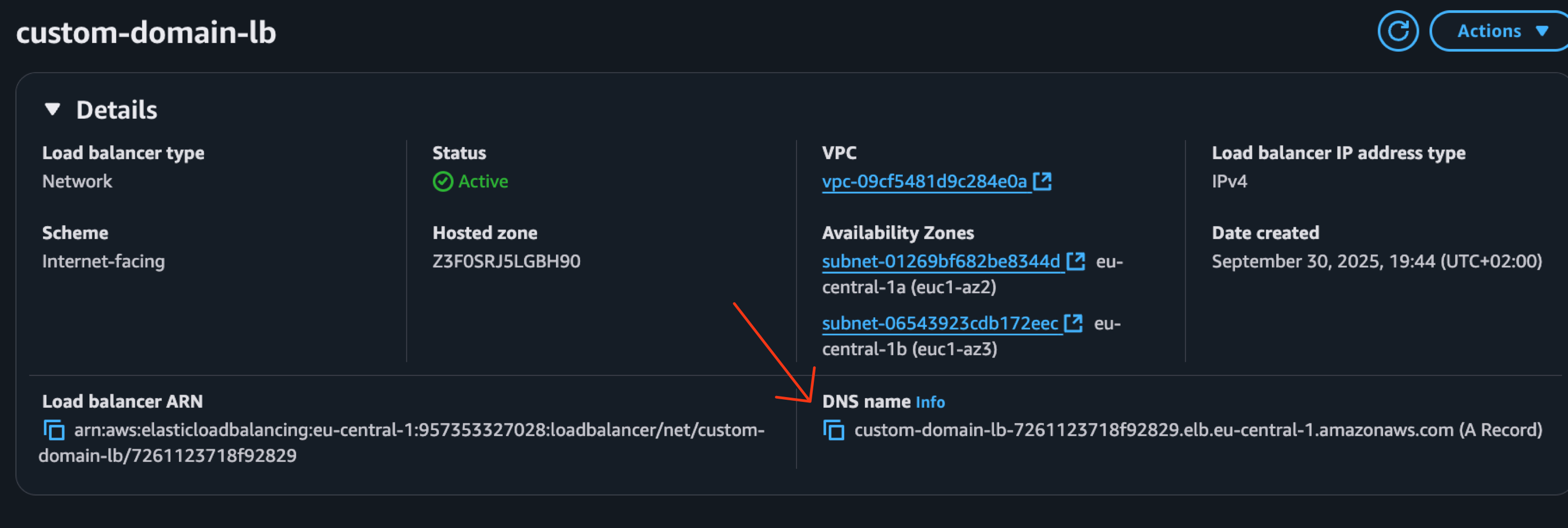
- Get Load Balancer DNS Name:
-
In the Load Balancer details, copy the DNS name.
-
In the Load Balancer details, copy the DNS name.
- Create DNS Records:
- In your DNS provider (Route 53, Cloudflare, etc.), create the following records: Main custom domain record:
-
Name: Your custom domain (e.g.,
ona.example.com). - Type: CNAME (or ALIAS if using Route 53).
- Value: Load Balancer DNS name. VSCode subdomain record:
-
Name:
vscode.prefix with your custom domain (e.g.,vscode.ona.example.com). - Type: CNAME (or ALIAS if using Route 53).
- Value: Load Balancer DNS name (same as above).
Note: Both DNS records must point to the same Load Balancer. The VSCode subdomain is required for VS Code Browser integration to work properly with your custom domain.
Step 4: Verify setup
- Wait for DNS propagation (typically 5-15 minutes).
- Access your custom domain in a browser:
https://ona.example.com. - Verify that:
- TLS certificate is valid.
- You can reach the Ona management plane.
- No certificate warnings appear.
Step 5: Update your SSO configuration
Update your SSO configuration to allow the new redirect URL using your custom domain:Step 6: Recreate your runner
Destroy any existing runners and create a new one by accessing the management plane from your custom domain. Follow the usual runner creation setup for AWS or for GCP. Why this is necessary: Runners are configured during creation with the management plane URL they should connect to. Existing runners will continue trying to connect via the old domain. Creating a new runner from your custom domain ensures it’s configured with the correct endpoint and can properly communicate with the management plane through your infrastructure.Step 7: Enforce custom domain access (Optional)
After completing the setup, you can optionally enable a policy to require all users to access Ona exclusively through your custom domain:- Navigate to Settings → Organization → Login and security.
- Enable Enforce custom domain access.
- All users, including organization admins, will be blocked from accessing via the default domain (
app.gitpod.io). - This ensures all traffic goes through your controlled infrastructure.
Users who are currently logged in with an active session can continue using the default domain until their session expires. The enforcement only applies to new login attempts.
Troubleshooting
Connection issues
If you cannot connect to your custom domain:- Verify DNS propagation using
digornslookup. - Check that the Load Balancer is in an Active state.
- Verify the target group or backend service shows healthy targets.
- Ensure security group rules (AWS) or firewall rules (GCP) allow traffic from your source.
Certificate errors
If you see certificate warnings:- AWS
- GCP
- Verify the ACM certificate covers both your main domain and the VSCode subdomain (
ona.example.comandvscode.ona.example.com). - Check that the certificate is attached to the Load Balancer listener.
- Ensure the certificate is valid and not expired.
- If using VS Code Browser, verify the certificate includes both the main domain and the VSCode subdomain in its Subject Alternative Names (SANs).
Performance issues
If you experience slow connections:- AWS
- GCP
- Verify the ALPN policy is set to HTTP/2 preferred on the Load Balancer listener.
- Check that you’ve selected at least 2 Availability Zones for high availability.
- Verify the VPC Endpoint is in an Available state.
Cloud-specific issues
- AWS
- GCP
AWS Account ID mismatchIf you see “AWS account ID mismatch” errors:
- Verify the VPC Endpoint was created in the same AWS account registered in your custom domain settings.
- Check the AWS account ID in Settings → Organization → Login and security → Domain & Access.
- If the account ID is incorrect, edit the custom domain configuration to update it.
- Verify the VPC Endpoint is connected to the Ona VPC Endpoint Service.
- Check that Proxy Protocol v2 is enabled on the Network Load Balancer target group.
- Ensure the VPC Endpoint is in an Available state.
- Verify the target group shows healthy targets.