Requires Enterprise plan. Contact sales for access.
- Setup - Deploy your GCP Runner with Terraform
- Access Requirements - Configure IAM permissions and network access
- Private GAR Images - Configure access to private Google Artifact Registry
- Runner Costs - Understand GCP Runner pricing and cost optimization
- Troubleshooting - Comprehensive troubleshooting and monitoring guide

Prerequisites
Before deploying your GCP Runner, ensure you have:- GCP Project with billing enabled, sufficient quotas for your expected workload, and required GCP APIs enabled
-
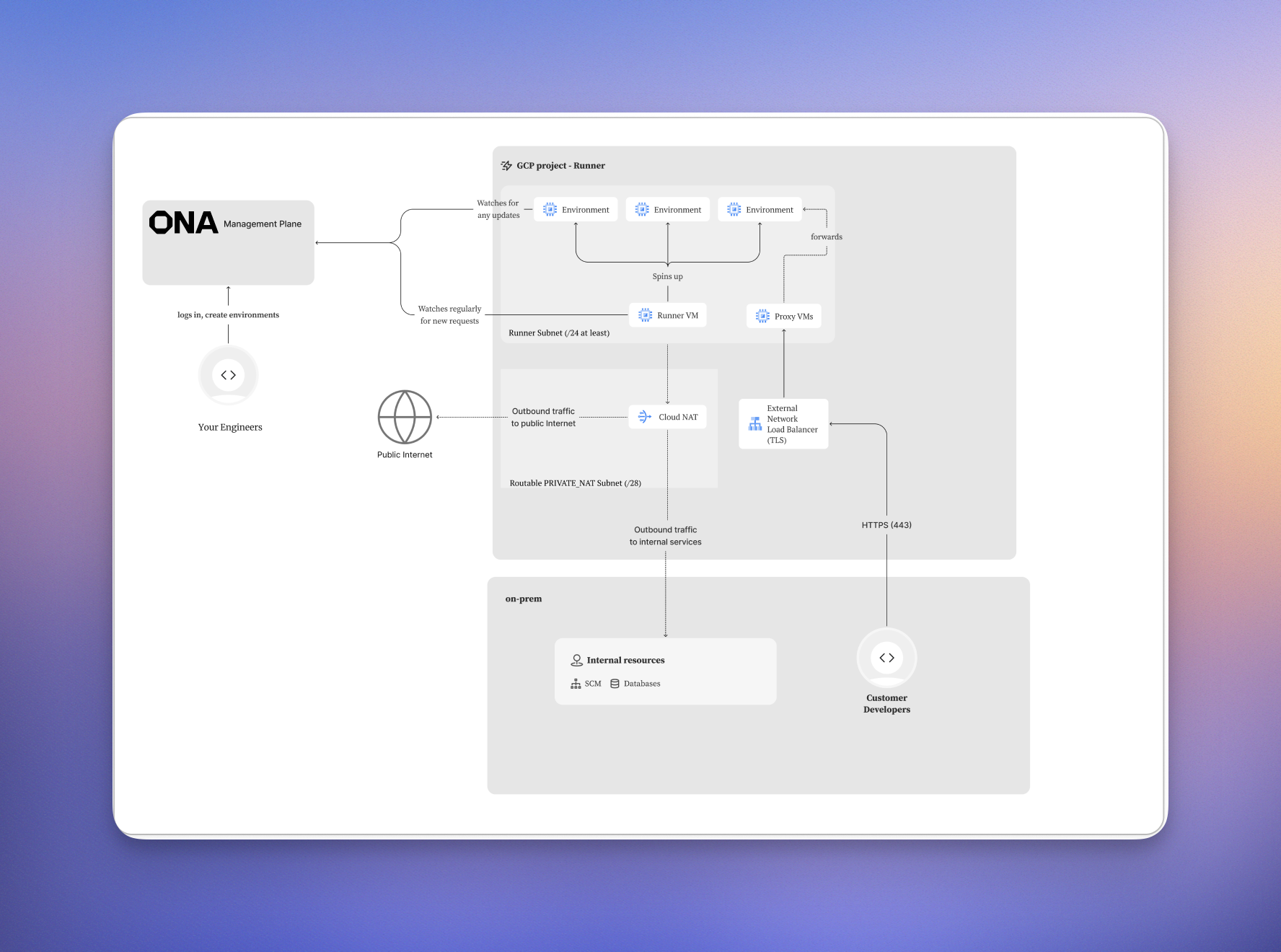
VPC and Networking - A custom VPC with properly configured subnets. Your GCP Runner deployment requires specific subnet configurations depending on your load balancer choice:
-
Runner Subnet (required for all deployments): Hosts both the runner service and development environment VMs. Must have Private Google Access enabled. Recommended CIDR:
/16for non-routable ranges (e.g.,10.0.0.0/16) for large deployments, or/24minimum for routable ranges requiring corporate network access. -
Proxy Subnet (required for Internal Load Balancer only): Reserved for internal load balancer proxy instances. Must have subnet purpose set to
REGIONAL_MANAGED_PROXY. Recommended CIDR:/27(32 IPs). Does NOT need to be routable from your corporate network. -
Routable Subnet (required for Internal Load Balancer only): Allocates the internal load balancer IP address. Must be routable from your corporate network (VPN, Interconnect, etc.). Recommended CIDR:
/28(16 IPs).
-
Runner Subnet (required for all deployments): Hosts both the runner service and development environment VMs. Must have Private Google Access enabled. Recommended CIDR:
- Domain Name that you control with DNS modification capabilities
-
SSL/TLS Certificate provisioned based on your load balancer choice:
- External LB: Certificate stored in Google Certificate Manager
- Internal LB: Certificate stored in Google Secret Manager with both certificate and private key
Load balancer configurations
The GCP Runner supports two load balancer configurations, each designed for different network architectures and security requirements.External Load Balancer (Default)
The external load balancer configuration provides internet-accessible development environments through Google Cloud’s global load balancer. This configuration is simpler to set up and doesn’t require additional networking configuration. Use Cases:- Development teams accessing environments from various locations
- Simplified setup with internet connectivity
- No additional network infrastructure required
- SSL certificate managed by Google Certificate Manager
- Public internet access to development environments
- Standard VPC subnet for development environments
Internal Load Balancer (Recommended for Enterprise)
The internal load balancer configuration keeps all traffic within your VPC and corporate network, providing the highest level of security and control. This configuration is ideal for enterprise environments with existing network infrastructure and security policies. Use Cases:- Enterprise environments with strict security requirements
- Corporate networks with VPN or interconnect access
- Zero internet exposure for development environments
- SSL certificate stored in Google Secret Manager (both certificate and private key)
- Dedicated proxy-only subnet with purpose REGIONAL_MANAGED_PROXY
- Corporate network connectivity to your GCP VPC (VPN, Interconnect, etc.)

Certificate requirements
SSL certificates are required for both load balancer configurations but have different storage and format requirements:External Load Balancer Certificate
- Storage: Google Certificate Manager
- Format: Managed certificate or uploaded certificate
- SANs required: Root domain (
yourdomain.com) and wildcard (*.yourdomain.com)
Internal Load Balancer Certificate
- Storage: Google Secret Manager
- Format: JSON object with both certificate and private key
- SANs required: Root domain (
yourdomain.com) and wildcard (*.yourdomain.com) - Secret format:
Next steps
- Setup - Deploy your GCP Runner with Terraform
- Access Requirements - Configure IAM permissions and network access