Pull request triggers require webhooks, which are available on the Enterprise plan only. See Plans and limits.
Supports GitHub and GitLab only. Use a service account for PR Automations to separate Automation activity from human work.
Configuration
Webhook
Select a webhook from the dropdown to connect this Automation to your Git provider. The webhook determines which repositories or organization the Automation listens to. If no webhooks exist yet, create one directly from the dropdown. See Webhooks for setup details.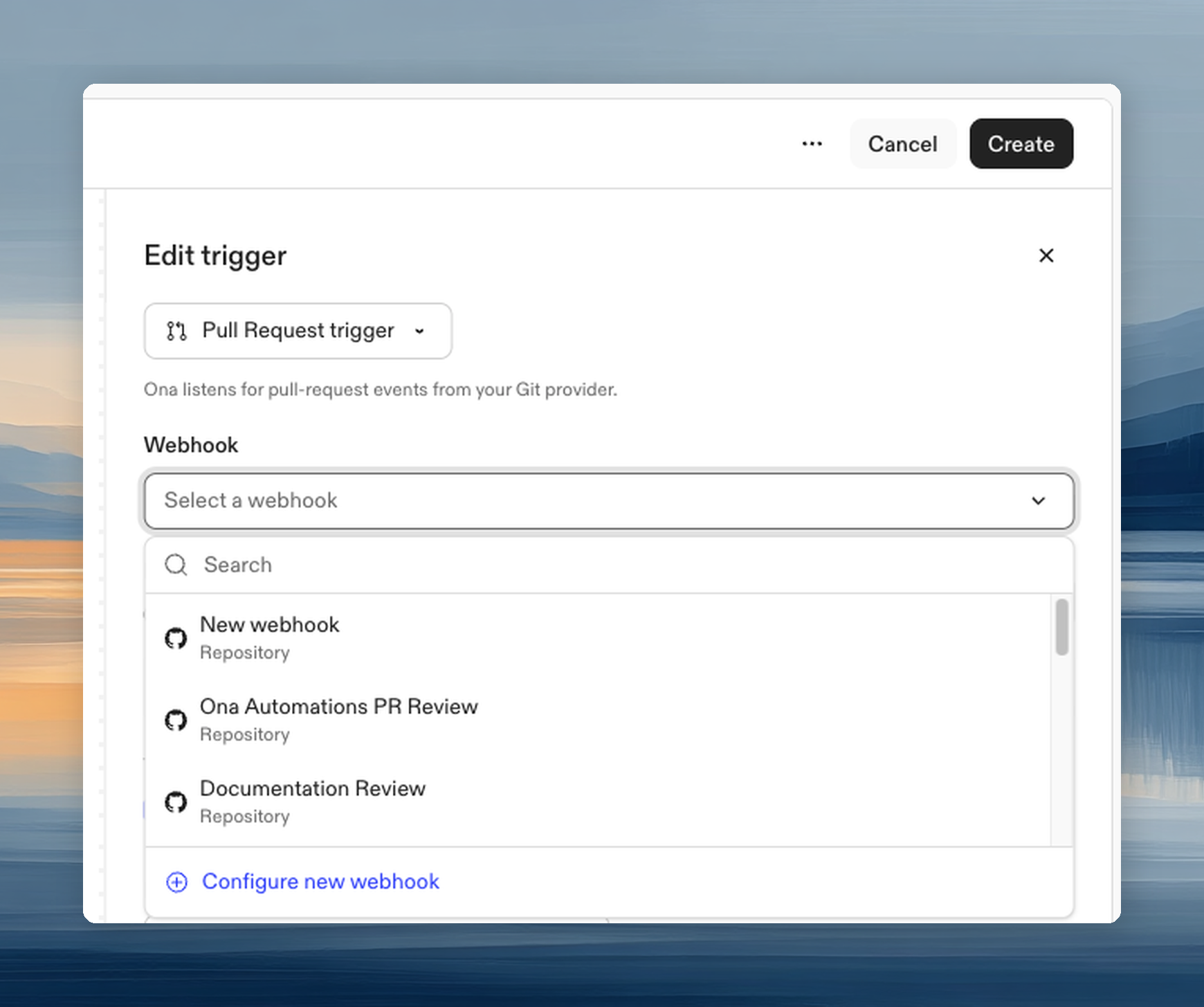
Target scope
- Projects: select projects. The Automation monitors all repositories within them.
- Repositories: use a search query to filter specific repositories.
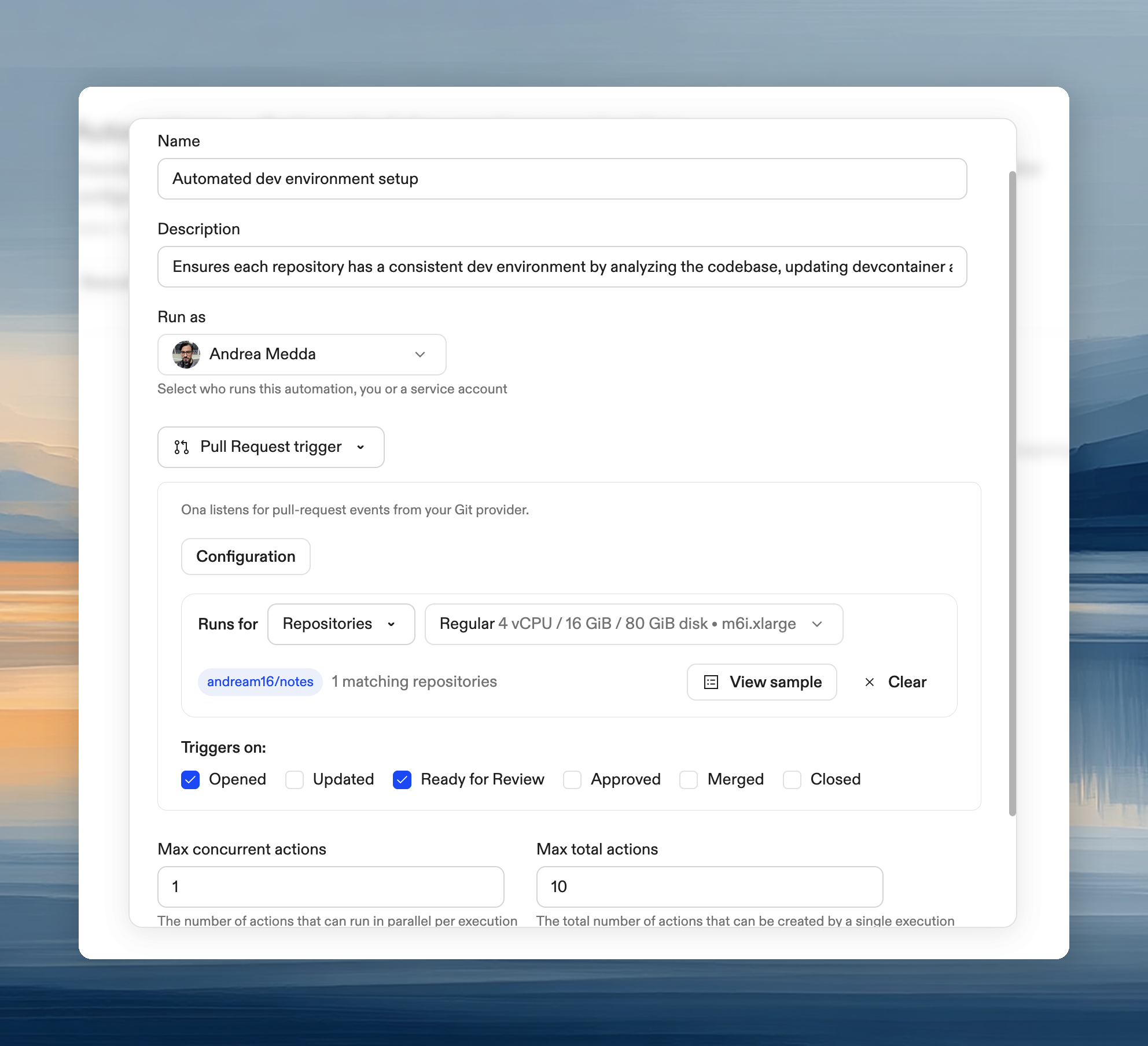
Events
| Event | When it fires |
|---|---|
| Opened | New PR created |
| Updated | New commits pushed |
| Ready for review | Draft marked ready |
| Approved | Reviewer approves |
| Merged | PR merged |
| Closed | PR closed without merge |
Next steps
- Webhooks: create and manage webhook endpoints
- Run an Automation
- Manual triggers
- Time-based triggers